#modern data warehouse
Explore tagged Tumblr posts
Text
Revolutionizing Analytics: How Modern Data Warehouses are Reshaping Decision-Making
In today's fast-paced and data-driven world, businesses face a constant influx of information from a multitude of sources. Extracting meaningful insights from this data is crucial for making informed decisions, optimizing operations, and gaining a competitive advantage. To meet the demands of data-driven decision-making, traditional data warehouses have evolved into modern data warehouses, revolutionizing the way organizations approach analytics. In this article, we will explore how modern data warehouses are reshaping decision-making and empowering businesses with actionable insights.
The Evolution of Data Warehousing: From Legacy to Modern
Traditional data warehouses, often housed on-premises, were designed to store and manage structured data from operational systems. They relied on batch processing and had limitations in terms of scalability and real-time data analytics. As data volumes exploded, these legacy systems struggled to keep up with the demand for faster insights and analysis.
Enter modern data warehouses, built on cloud-based infrastructure. They represent a paradigm shift in data management and analytics, addressing the challenges of data scalability, real-time processing, and diverse data types. Modern data warehouses empower businesses with the capability to process vast amounts of data quickly and efficiently, transforming raw data into actionable insights.
Key Features of Modern Data Warehouses:
Scalability and Elasticity: Cloud-based modern data warehouses offer scalable and elastic resources. Organizations can adjust their computing power and storage based on demand, ensuring optimal performance during peak usage periods.
Real-time Data Analytics: Modern data warehouses support real-time data processing, enabling businesses to analyze data as it is generated. This capability provides organizations with up-to-the-minute insights, facilitating timely decision-making.
Data Integration: Modern data warehouses excel at integrating data from various sources, including structured, semi-structured, and unstructured data. They can seamlessly ingest data from databases, applications, IoT devices, social media, and more.
Cost Efficiency: Cloud-based data warehouses follow a pay-as-you-go model, eliminating the need for upfront infrastructure investments. This cost-effective approach makes data warehousing accessible to organizations of all sizes.
Advanced Analytics Capabilities: Modern data warehouses offer built-in support for advanced analytics, including machine learning and AI. This empowers organizations to derive deeper insights and uncover hidden patterns in their data.
Reshaping Decision-Making with Modern Data Warehouses:
Faster Insights: Modern data warehouses process data in real-time, reducing the time between data generation and analysis. Decision-makers can access the latest information, enabling faster and more informed decision-making.
Data-Driven Strategy: With comprehensive data integration and analysis capabilities, modern data warehouses enable organizations to develop data-driven strategies. By relying on empirical evidence rather than intuition, businesses can refine their approaches and achieve better outcomes.
Identifying Trends and Patterns: Modern data warehouses facilitate in-depth analysis of large datasets, helping organizations identify trends and patterns that may have gone unnoticed in traditional data warehousing systems. These insights enable businesses to proactively respond to market changes and customer preferences.
Personalized Customer Experiences: By leveraging advanced analytics, modern data warehouses enable businesses to create personalized customer experiences. They can understand customer preferences, predict behavior, and offer tailored products and services.
Optimizing Operations: Data-driven decision-making extends beyond customer experiences. Organizations can use data insights to optimize internal operations, streamline processes, and enhance overall efficiency.
FAQ about Modern Data Warehouses:
Q1: Can small and medium-sized businesses benefit from modern data warehouses?
A1: Absolutely. Modern data warehouses, with their scalability and cost efficiency, are accessible to organizations of all sizes. Small and medium-sized businesses can leverage modern data warehouses to gain actionable insights, make informed decisions, and drive growth.
Q2: Do modern data warehouses replace business intelligence tools?
A2: No, modern data warehouses complement business intelligence (BI) tools. While data warehouses store and manage data, BI tools provide visualization and reporting capabilities, allowing users to explore data and create dashboards.
Q3: Are modern data warehouses secure?
A3: Yes, modern data warehouses prioritize data security. Cloud-based data warehouses implement robust security measures, including encryption, access controls, and compliance features, to protect sensitive information.
Q4: How difficult is it to migrate from a traditional data warehouse to a modern one?
A4: Data warehouse migration requires careful planning and execution. The complexity of the migration process depends on factors such as the size of the data, data structure, and the technology used. However, with proper planning and the assistance of experts, the migration can be seamless and rewarding.
Q5: What impact does data warehouse modernization have on data governance?
A5: Data warehouse modernization strengthens data governance practices. Modern data warehouses offer better data quality, standardization, and consistency, making it easier for organizations to adhere to data governance policies and compliance regulations.
Conclusion
Modern data warehouses have revolutionized the way organizations approach data analytics and decision-making. With real-time data processing, scalability, and advanced analytics capabilities, modern data warehouses empower businesses with timely, actionable insights. As more organizations embrace data-driven strategies, modern data warehouses will continue to play a pivotal role in shaping the future of business intelligence. By leveraging the power of data and analytics, businesses can unlock new opportunities, optimize operations, and stay ahead in the increasingly competitive digital landscape. Embracing the potential of modern data warehouses is not just a step towards staying relevant; it is the key to thriving in the data-driven era.
0 notes
Text

Data Warehouse Consulting Services | Modern Data Infrastructure
Optimize your data strategy with Goognu’s Data Warehouse Consulting Services. We help design, build, and manage scalable data warehouse solutions that ensure fast, secure, and reliable access to critical business insights — empowering smarter decision-making.
0 notes
Text
Big Data vs. EDW: Can Modern Analytics Replace Traditional Data Warehousing?
As organizations increasingly rely on data to drive business decisions, a common question arises: Can Big Data replace an EDW (Enterprise Data Warehouse)? While both play crucial roles in managing data, their purposes, architectures, and strengths differ. Understanding these differences can help businesses decide whether Big Data technologies can entirely replace an EDW or if a hybrid approach is more suitable.

What Does EDW Stand for in Data?
An EDW or Enterprise Data Warehouse is a centralized repository where organizations store structured data from various sources. It supports reporting, analysis, and decision-making by providing a consistent and unified view of an organization’s data.
Big Data vs. EDW: Key Differences
One of the primary differences between Big Data and enterprise data warehousing lies in their architecture and the types of data they handle:
Data Type: EDWs typically manage structured data—information stored in a defined schema, such as relational databases. In contrast, Big Data platforms handle both structured and unstructured data (like text, images, and social media data), offering more flexibility.
Scalability: EDWs are traditionally more rigid and harder to scale compared to Big Data technologies like Hadoop and Spark, which can handle massive volumes of data across distributed systems.
Speed and Performance: EDWs are optimized for complex queries but may struggle with the vast amounts of data Big Data systems can process quickly. Big Data’s parallel processing capabilities make it ideal for analyzing large, diverse data sets in real time.
Big Data Warehouse Architecture
The Big Data warehouse architecture uses a distributed framework, allowing for the ingestion, storage, and processing of vast amounts of data. It typically consists of:
Data Ingestion Layer: Collects and streams data from various sources, structured or unstructured.
Storage Layer: Data is stored in distributed systems, such as Hadoop Distributed File System (HDFS) or cloud storage, allowing scalability and fault tolerance.
Processing Layer: Tools like Apache Hive and Apache Spark process and analyze data in parallel across multiple nodes, making it highly efficient for large data sets.
Visualization and Reporting: Once processed, data is visualized using BI tools like Tableau, enabling real-time insights.
This architecture enables businesses to harness diverse data streams for analytics, making Big Data an attractive alternative to traditional EDW systems for specific use cases.
Can Big Data Replace an EDW?
In many ways, Big Data can complement or augment an EDW, but it may not entirely replace it for all organizations. EDWs excel in environments where structured data consistency is crucial, such as financial reporting or regulatory compliance. Big Data, on the other hand, shines in scenarios where the variety and volume of data are critical, such as customer sentiment analysis or IoT data processing.
Some organizations adopt a hybrid model, where an EDW handles structured data for critical reporting, while a Big Data platform processes unstructured and semi-structured data for advanced analytics. For example, Netflix uses both—an EDW for business reporting and a Big Data platform for recommendation engines and content analysis.
Data-Driven Decision Making with Hybrid Models
A hybrid approach allows organizations to balance the strengths of both systems. For instance, Coca-Cola leverages Big Data to analyze consumer preferences, while its EDW handles operational reporting. This blend ensures that the company can respond quickly to market trends while maintaining a consistent view of critical business metrics.
Most Popular Questions and Answers
Questions: Can Big Data and EDW coexist?
Answers: Yes, many organizations adopt a hybrid model where EDW manages structured data for reporting, and Big Data platforms handle unstructured data for analytics.
Questions: What are the benefits of using Big Data over EDW?
Answers: Big Data platforms offer better scalability, flexibility in handling various data types, and faster processing for large volumes of information.
Questions: Is EDW still relevant in modern data architecture?
Answers: Yes, EDWs are still essential for organizations that need consistent, reliable reporting on structured data. However, many companies also integrate Big Data for advanced analytics.
Questions: Which industries benefit most from Big Data platforms?
Answers: Industries like retail, healthcare, and entertainment benefit from Big Data’s ability to process large volumes of unstructured data, providing insights that drive customer engagement and innovation.
Questions: Can Big Data handle structured data?
Answers: Yes, Big Data platforms can process structured data, but their true strength lies in handling unstructured and semi-structured data alongside structured data.
Conclusion
While Big Data offers impressive capabilities in handling massive, diverse data sets, it cannot completely replace the functionality of an Enterprise Data Warehouse for all organizations. Instead, companies should evaluate their specific needs and consider hybrid architectures that leverage the strengths of both systems. With the right strategy, businesses can harness both EDWs and Big Data to make smarter, faster decisions and stay ahead in the digital age.
Browse Related Blogs –
From Data to Intelligence: How Knowledge Graphs are Shaping the Future
AI to the Rescue: Revolutionizing Product Images in the E-Commerce Industry
0 notes
Text
Implementing Data Mesh on Databricks: Harmonized and Hub & Spoke Approaches
Explore the Harmonized and Hub & Spoke Data Mesh models on Databricks. Enhance data management with autonomous yet integrated domains and central governance. Perfect for diverse organizational needs and scalable solutions. #DataMesh #Databricks

View On WordPress
#Autonomous Data Domains#Data Governance#Data Interoperability#Data Lakes and Warehouses#Data Management Strategies#Data Mesh Architecture#Data Privacy and Security#Data Product Development#Databricks Lakehouse#Decentralized Data Management#Delta Sharing#Enterprise Data Solutions#Harmonized Data Mesh#Hub and Spoke Data Mesh#Modern Data Ecosystems#Organizational Data Strategy#Real-time Data Sharing#Scalable Data Infrastructures#Unity Catalog
0 notes
Text
Data Warehouse Modernization Strategies You Must Know in 2024

Data warehouse modernization encompasses various approaches tailored to your business requirements. Explore the blog to learn the top strategies for modernizing the data warehouse.
0 notes
Text
Axolt: Modern ERP and Inventory Software Built on Salesforce
Today’s businesses operate in a fast-paced, data-driven environment where efficiency, accuracy, and agility are key to staying competitive. Legacy systems and disconnected software tools can no longer meet the evolving demands of modern enterprises. That’s why companies across industries are turning to Axolt, a next-generation solution offering intelligent inventory software and a full-fledged ERP on Salesforce.
Axolt is a unified, cloud-based ERP system built natively on the Salesforce platform. It provides a modular, scalable framework that allows organizations to manage operations from inventory and logistics to finance, manufacturing, and compliance—all in one place.
Where most ERPs are either too rigid or require costly integrations, Axolt is designed for flexibility. It empowers teams with real-time data, reduces manual work, and improves cross-functional collaboration. With Salesforce as the foundation, users benefit from enterprise-grade security, automation, and mobile access without needing separate platforms for CRM and ERP.
Smarter Inventory Software Inventory is at the heart of operational performance. Poor inventory control can result in stockouts, over-purchasing, and missed opportunities. Axolt’s built-in inventory software addresses these issues by providing real-time visibility into stock levels, warehouse locations, and product movement.
Whether managing serialized products, batches, or kits, the system tracks every item with precision. It supports barcode scanning, lot and serial traceability, expiry tracking, and multi-warehouse inventory—all from a central dashboard.
Unlike traditional inventory tools, Axolt integrates directly with Salesforce CRM. This means your sales and service teams always have accurate availability information, enabling faster order processing and better customer communication.
A Complete Salesforce ERP Axolt isn’t just inventory software—it’s a full Salesforce ERP suite tailored for businesses that want more from their operations. Finance teams can automate billing cycles, reconcile payments, and manage cash flows with built-in modules for accounts receivable and payable. Manufacturing teams can plan production, allocate work orders, and track costs across every stage.
86 notes
·
View notes
Text
Paper cuts
|Jelsa, Modern AU, Enemies with Benefits, Fake dating, Forced Proximity|

Agent Elsa Stenford [NID-SO-ES-07] — Operation Report Upload Log
—Logged into secure terminal: Vienna Safehouse Terminal-2
—Date: 2022-07-08
—Time (UTC): 23:16
—Connected to secure node: NIDNet
—Report file: OP_SILENTRAVEN_AAR.enc
—Encryption status: Secured with NID Master Key — encryption signature verified (Checksum ID: F1A5-7C9B)
—Recipient(s): Jack Frost, Section Chief Special Operations (SO-92A), Acting Division Supervisor (DS-4), National Intelligence Directorate
—Transmission channel: Priority-One Secure Uplink (Classified Level: TOP SECRET)
—Transmission status: COMPLETE — audit log updated (Reference Log ID: ES07-0525-2214)
—Backup status: Encrypted local backup stored (Partition ES-07-SAFE); master copy uploaded to Central Ops Archive (Vault-4)
—Field confirmation: Agent ES-07 signed digital attestation; no tampering detected; self-authentication successful
Note: Automatic alert dispatched to Division Supervisor terminal. Clearance authentication required upon access.
---------------------------
Operation Silent Raven is an ongoing mission targeting a covert illicit arms trafficking network operating primarily in South Carolina. [Flag—Acting supervisor: Delete ‘ongoing mission’ — this is filler from someone unfamiliar with concise reporting. Vague and redundant.] This report details recent operational progress, intelligence collection, and actionable recommendations. [Flag—Acting supervisor: You clearly do not understand report structure. This useless sentence wastes time and space.]
The primary objective is to identify, monitor, and dismantle the arms trafficking chain responsible for the flow of small arms and light weapons through various transit points in the region. [Flag—Acting supervisor: Restating obvious without any specifics or measurable targets reflects poor understanding of operational goals. Omit.] HUMINT sources have verified the existence of a new maritime transit corridor utilizing the seaport. [Flag—Acting supervisor: “HUMINT sources” is lazy projection. You apparently cannot be trusted to identify sources properly. Brackets demonstrate careless drafting.] SIGINT intercepted encrypted communications that suggest coordination between traffickers and local facilitators. [Flag—Acting supervisor: ‘Suggest’ is weak speculation, unbefitting a professional intelligence report. Either confirm or remove this guesswork.]
Financial forensics have traced suspicious funds transfers totaling approximately $8 million USD linked to traffickers. [Flag—Acting supervisor: Provide specifics or this bland, meaningless statement reveals superficial analysis.] Technical surveillance detected multiple covert meetings in [Urban Centers], corroborated by photographic evidence. [Flag—Acting supervisor: Using placeholders signals either incompetence or utter disregard for accuracy.] On 2022-06-21, interdiction team, operating with local law enforcement, seized 250 illegal firearms at the port city warehouse. [Flag—Acting supervisor: Poorly structured sentence; the muddled passive voice further obscures the facts you apparently cannot clearly present.] Two principal suspects were detained, providing critical intelligence that identified higher-level facilitators. [Flag—Acting supervisor: Passive construction and vague attribution further demonstrate your failure to take ownership of this data.]
Informant “Falcon” supplied actionable intelligence regarding a planned arms shipment scheduled for early June. [Flag—Acting supervisor: Finally, a clear statement, but unfortunately, it’s buried among verbosity and filler.] Operational security protocols were heightened after detecting possible surveillance by hostile intelligence actors. [Flag—Acting supervisor: ‘Possible’ surveillance indicates your uncertainty and it undermines the entire assessment and betrays inadequate situational awareness.] The network disruption has temporarily halted major arms transfers. [Flag—Acting supervisor: ‘Temporarily’ suggests you lack the insight or confidence to forecast outcomes. Such ambiguity is unacceptable.]
Surveillance and intelligence collection continue focusing on secondary facilitators and financing channels. [Flag—Acting supervisor: Non-specific, passive phrasing again. You appear unable to report with decisiveness or clarity.] Coordination with allied intelligence agencies is ongoing to leverage broader interdiction efforts. [Flag—Acting supervisor: “Allied intelligence agencies” — weak and meaningless. Omit.] Risk assessment indicates elevated threat levels against NID assets involved in this operation. [Flag—Acting supervisor: Without elaboration, this statement is worthless. The absence of detail is either negligence or incompetence. I’m leaning towards the latter, although the first one also seems to be your defining trait.] Approve expansion of covert operations targeting secondary facilitators and financiers. [Flag—Acting supervisor: Recommendations lack essential resource planning and rationale, further exposing your inexperience.] Request additional SIGINT and counter-surveillance resources. [Flag—Acting supervisor: ‘Additional’ is meaningless without quantification. This sloppy request reflects poor operational understanding.] Initiate an inter-agency task force to address cross-border financing and logistics. [Flag—Acting supervisor: Unsubstantiated recommendation with no defined objectives — this is amateurish.] Continue monitoring and protection of key HUMINT sources and operatives. [Flag—Acting supervisor: Failing to specify protection protocols reflects a dangerous oversight on your part.] Attachments include interdiction team after-action report, financial transaction analyses, SIGINT intercept summaries, and photographic documentation of seized arms and facilities. [Flag—Acting supervisor: Referencing attachments without actual inclusion indicates either incompetence or disregard for proper reporting. Which one is it?]
Flag—Acting supervisor: This report is miserably inadequate and reflects a disturbing lack of professionalism and capability. The careless placeholders, vague assertions, passive voice, and speculative language betray your failure to grasp even the basic standards of intelligence reporting. Such work not only wastes time but actively hampers operational efficiency. REWRITE.
---------------------------
Secure Directive
From: Jack Frost
[Code: NID-SO-JF-01]
Section Chief, Special Operations / Acting Division Supervisor [Code SO-92A/DS-4]
To: Agent Elsa Stenford [Code:NID-SO-ES-07]
Subject: RE: Report Review – Operation Silent Raven
Classification: TOP SECRET // EYES ONLY
Agent Stenford,
Your submitted report for Operation Silent Raven is wholly inadequate and reflects a concerning lack of analytical rigor, operational discipline, and professional attention. The presence of unresolved placeholders, vague assertions, speculative conclusions, and critical data gaps is unacceptable at this operational level and wastes valuable time and resources.
This level of oversight is incompatible with the standards expected from an intelligence officer assigned to this unit. You are to:
1. Eliminate all placeholders and provide verified, cross-checked intelligence.
2. Remove speculative or assumptive language; include only confirmed, actionable data.
3. Rewrite sections for clarity, precision, and direct accountability — passive formulations are unacceptable.
4. Deliver detailed, concrete descriptions of sources, operational locations, timelines, and outcomes without ambiguity.
5. Ensure all referenced materials are attached, properly labeled, and internally consistent.
6. Strengthen recommendations by specifying exact resource needs, operational impacts, and executable directives.
7. Fully address risk assessments with defined threats, probability ratings, and specific mitigation strategies.
The supervisor-annotated version of your report (File ID: SR-Report-Rev1-JF) has been uploaded to the secure review system. You are to address all marked corrections and resubmit the fully corrected report no later than 1800 hours today. No further extensions will be granted.
Jack Frost
[Code: NID-SO-JF-01]
Section Chief, Special Operations (SO-92A)
Acting Division Supervisor (DS-4)
National Intelligence Directorate
---------------------------
Agent Elsa Stenford [Code: NID-SO-ES-07] — Report Upload Log (Revised Submission)
—Logged into secure terminal: Vienna Safehouse Terminal-2
—Date: 2022-07-09
—Time (UTC): 17:38
—Connected to secure node: NIDNet
—Report file: OP_SIENTRAVEN_AAR_v2.enc
—Encryption status: Secured with NID Master Key — encryption signature verified (Checksum ID: F1A9-7C3B-R2)
—Recipient(s): Jack FrostJack Frost (NID-SO-JF-01), Section Chief Special Operations (SO-92A), Acting Division Supervisor (DS-4), National Intelligence Directorate
—Transmission channel: Priority-One Secure Uplink (Classified Level: TOP SECRET)
—Transmission status: COMPLETE — audit log updated (Reference Log ID: ES07-0525-2316-R2)
—Backup status: Encrypted local backup stored (Partition ES-07-SAFE); master copy uploaded to Central Ops Archive (Vault-4, Revised Submission Folder)
—Field confirmation: Agent ES-07 signed digital attestation; no tampering detected; self-authentication successful
Note: Automatic alert dispatched to Division Supervisor terminal. Clearance authentication required upon access. Revision flag registered under Audit Protocol 4B.
---------------------------
Secure Directive
From: Jack Frost [Code: NID-SO-JF-01]
Section Chief, Special Operations / Acting Division Supervisor [Code: SO-92A/DS-4]
To: Elsa Stenford [Code: NID-SO-ES-07]
Subject: RE: Secure Directive – Operation Silent Raven Report (Revised Submission)
Agent Stenford,
I have completed my review of your revised report on Operation Silent Raven. The annotated document is attached under:
Attachment: SilentRaven_Rev2_ES07_JFcomments.secure
To be precise: this submission remains below acceptable operational standards. Your continued use of speculative phrasing, unsupported assertions, and vague recommendations demonstrates a concerning lack of analytical discipline. This is not a matter of inexperience. You are not a trainee, Agent. At your level and position, you are expected to understand and apply the standards of rigor, precision, and clarity required in all agency reporting. That expectation is not optional.
Your report exhibits repeated failures:
1. Speculative language where concrete analysis is required;
2. Lack of referenced source attachments, despite multiple directives;
3. Unquantified risk assessments, absent methodological support;
4. Action recommendations devoid of operational specificity.
This is not a learning exercise nor is it a second chance, Agent Stenford. I should not be required to remind you of the foundational protocols governing intelligence reporting. You are expected to deliver work that reflects your clearance level, your operational rank, and your assigned responsibilities — without need for remedial oversight.
You are hereby directed to produce a final, fully compliant, actionable revision and submit it under secure protocol no later than 1300 hours tomorrow. Failure to meet this directive will result in formal escalation to the Division Office for immediate performance review. There will be no further instructions, no extended clarifications, and no tolerance for repeated submission failures.
Jack Frost [Code: NID-SO-JF-01]
Section Chief, Special Operations (SO-92A)
Acting Division Supervisor (DS-4)
National Intelligence Directorate
*
Operation Silent Raven: A report
1. Executive Summary:
—The target group’s network activity has intensified in the last 72 hours, with encrypted communications suggesting a planned operation within the capital region. [Flag—Acting supervisor: “Suggesting” is a charming euphemism for “guessing.” Precision is not your forte, is it?]
—HUMINT sources indicate the possible involvement of an external actor, potentially destabilizing regional security. [Flag—Acting supervisor: “Possible” and “potentially” — a truly inspiring display of hedging. I applaud your commitment to ambiguity.] While these indicators warrant heightened surveillance, conclusive evidence regarding the exact nature and timing of the planned event remains unconfirmed. [COMMENT: I look forward to the day when ‘unconfirmed’ is replaced by ‘confirmed.’ Continue taking baby steps, we’re all here to babysit you and instruct on every level, not to do our job.]
2. Intelligence Sources:
SIGINT: Intercepted encrypted transmissions on frequencies 8.1 GHz to 8.3 GHz, believed to originate from multiple cell towers in the downtown sector. [Flag—Acting supervisor: “Believed.” A masterclass in non-committal language. Bold. Yet, it fails to meet the minimum standards of verification.] Metadata analysis aligns with previous hostile activity patterns.
[Flag—Acting supervisor: Please specify the parameters of your analysis. Otherwise, it reads as a hopeful suggestion rather than intelligence.]
HUMINT: Confidential informant reported unusual meetings near industrial sector 4. Reliability assessed as moderate; corroborating SIGINT incomplete. [Flag—Acting supervisor: ‘Moderate’ is an imaginative way of saying ‘I’m not sure.’ The agency appreciates your creativity but prefers facts.]
IMINT: Limited satellite imagery from 23-25 MAY shows increased vehicular movements near potential staging areas, but imagery quality insufficient for identification of personnel or equipment. [Flag—Acting supervisor: Including non-identifiable imagery is an excellent way to fill pages. Whether it aids operations is another matter. But who cares?]
3. Operational Assessment:
The convergence of SIGINT and HUMINT suggests preparatory steps for an operation targeting critical infrastructure. [Flag—Acting supervisor: ‘Suggests’ again. I see a pattern. Perhaps next time try ‘confirms’ or ‘demonstrates.’] Risk assessment places the likelihood of attack at moderate (probability 0.55), with potential impact categorized as high due to target significance. [Flag—Acting supervisor: : Quantify your methodology. Numbers plucked from thin air are less useful than no numbers at all.] Recommended actions include intensifying electronic surveillance, deploying field assets for direct observation, and liaising with allied cyber-intelligence units to monitor digital footprints. [Flag—Acting supervisor: Vague directives are the hallmark of an inexperienced analyst. Details and accountability please.]
4. Recommendations:
Immediate deployment of SIGINT intercept teams in the identified frequency bands. Enhanced HUMINT debriefings with source ES-27 to confirm meeting details. [Flag—Acting supervisor: The lack of specificity here suggests an admirable level of trust in the reader’s imagination.] Coordination with Cyber Ops for real-time network traffic analysis. [Flag—Acting supervisor: Nomenclature alone does not constitute a plan. Flesh this out.]
Notes [Acting Supervisor] :
—Formatting inconsistent with NID operational report guidelines. You’ve transformed a simple formatting standard into an elusive art form. Bravo.
—Failure to attach referenced supporting materials AGAIN. This recurring omission hinders operational efficacy. Consider attaching documents next time.
—In conclusion, REWRITE.
---------------------------
Agent [Code: NID-SO-ES-07] — Field Report Upload Log (Revised Submission)
—Logged into secure terminal: Vienna Safehouse Terminal-2
—Date: 2022-07-10
—Time (UTC): 13:00
—Connected to secure node: NIDNet
—Report file: OP_SILENTRAVEN_AAR_v3.enc
—Encryption status: Secured with NID Master Key — encryption signature verified (Checksum ID: F1A9-7C3B-R2)
—Recipient(s): Jack Frost, Section Chief Special Operations (SO-92A), Acting Division Supervisor (DS-4), NID
—Transmission channel: Priority-One Secure Uplink (Classified Level: TOP SECRET)
—Transmission status: COMPLETE — audit log updated (Reference Log ID: ES07-0710-1300-R2)
—Backup status: Encrypted local backup stored (Partition ES-07-SAFE); master copy uploaded to Central Ops Archive (Vault-4, Revised Submission Folder)
—Field confirmation: Agent ES-07 signed digital attestation; no tampering detected; self-authentication successful
Note: Automatic alert dispatched to Division Supervisor terminal. Clearance authentication required upon access. Revision flag registered under Audit Protocol 4B.
---------------------------
Secure Directive
From: Jack Frost [NID-SO-JF-01]
Section Chief, Special Operations / Acting Division Supervisor [Code: NID-SO-92A/DS-4]
To: Elsa Stenford [Code: NID-SO-ES-07]
Subject: RE: Secure Directive – Operation Silent Raven Report , Revocation of Field Authority and Immediate Reassignment
Agent Stenford,
I was informed last afternoon that due to shifting operational priorities, the report in question [Ops Silent Raven] is no longer required.
After review of your latest submission — the revised report you provided earlier today — I must formally acknowledge that the material remains below acceptable operational standards. While I did not realistically anticipate any significant improvement, it is nonetheless disappointing that even after detailed corrective input, your output failed to meet the basic analytical and procedural thresholds expected of an intelligence officer at your level.
However, the time I was forced to expend personally correcting and annotating your repeated errors constitutes an unacceptable diversion of supervisory resources. You have now occupied more of this division’s time and attention than your current role warrants.
Accordingly, effective immediately, your independent field authority is revoked. You are reassigned to trailing support under Intelligence Officer Logan Parrish [CODE: NID-SO-LP-33], Team Blue. While Officer Parrish holds the same formal rank as you, his superior reliability and competence justify his lead role in this arrangement.
You are to operate strictly under Officer Parrish’s direction, with no independent decision-making or external communications without prior clearance. This corrective assignment will remain in place until further notice and serves as a necessary intervention to address the persistent deficits in your performance.
You are to report to Team Blue at 07:00 hours tomorrow, prepared and fully compliant. Written acknowledgment of this directive is required by 16:00 hours today. Noncompliance will result in immediate formal disciplinary action.
Jack Frost [Code: NID-SO-JF-01]
Section Chief, Special Operations (SO-92A)
Acting Division Supervisor (DS-4)
National Intelligence Directorate
---------------------------
Elsa Stenford read the message over and over again, because she knew it wasn’t serious. It must be a mistake. A joke. That’s what it was. Maybe if she read it again, it would change, it would shift and it would fix itself. So she read it, the words physically burning her, over and over again, but it stayed the same. She just stared at it, mouth hanging open, eyes wide with shock, unblinking.
“Elsa?” Merida’s voice shattered the silence in her head. “Are you—”
“THAT MISERABLE FUCKING BASTARD! THAT FUCKING—” She stopped herself, but there was just too much rage and hate in her, enough for her to combust and paint the walls red. "FUCKING PIECE OF SCUM! I FUCKING HATE HIM, THAT USELESS, ARROGANT, SLIMY RAT!"
---------------------------
#jelsa#jelsa in 2025#jelsa fanfiction#jelsa au#jack frost#queen elsa#frozen#rise of the guardians#ao3#rotg#rotg jack frost#disney frozen#elsa frozen#jackson overland frost#elsa x jack frost#jack frost x elsa#enemies to lovers#enemies with benefits#workplace#forced proximity#ao3 fanfic#anna frozen#kristanna#frozen fever#merida dunbroch#angst#merida#brave#rotbtd#disney
20 notes
·
View notes
Text
Military Leaders Warn Conservative Budget Plans Put Country At Risk


WASHINGTON (AP) — Military service leaders told senators Wednesday that passing a temporary budget that keeps defense spending largely flat will hurt readiness and efforts to modernize the armed forces. The vice chiefs of the Army, Navy, Marine Corps and Air Force said that if they don’t get additional funding, they at least need the flexibility to shift money to ensure priorities are covered. Congress has been unable to get through a full 2025 fiscal year budget and instead has passed temporary stopgap measures that largely keep funding at 2024 levels. A bill passed Tuesday by the House would increase defense spending by about $6 billion and trim $13 billion in non-defense spending, which are rather flat changes for both categories when compared with an overall topline of nearly $1.7 trillion in discretionary spending. The legislation now moves to the Senate. This would be the first year that Congress hasn’t passed a defense spending bill and will instead use a full-year continuing resolution, the military leaders said. They said that continuing the 2024 budget lines doesn’t allow the services to start new contracts, including for weapon modernization or housing and other improvements. “Ultimately, the Army can afford a large, ready or modern force, but with the current budget, it cannot afford all three,” Gen. James Mingus, vice chief of staff of the Army, told the Senate Armed Services readiness subcommittee. “Either we provide soldiers the capabilities needed to win or accept greater risks in other areas.” He warned that the Army will pay for those risks down the road, “not in delayed projects or budget adjustments, but in real-world battlefield consequences. We need to invest in the things and training our soldiers need for the next fight, not the last fight.” Other service leaders echoed his warning, noting that shortfalls in shipbuilding, maintenance and sustainment affect both the Navy and the Marine Corps. Adm. James Kilby, vice chief of naval operations, said this “will slow shipbuilding, including our amphibious warships.” Marine leaders have long complained about the lack of critically needed amphibious ships that can transport Marines at sea to combat. As of Wednesday morning, said Gen. Christopher Mahoney, assistant commandant of the Marine Corps, just 13 of the Navy’s 32 amphibious ships were available for use. And Air Force Lt. Gen. Adrian L. Spain, deputy chief of staff, said the continuing resolution will affect combat readiness in his service “to the tune of about $4 billion.” President Donald Trump and Defense Secretary Pete Hegseth have both spoken extensively about the need to focus on military readiness and lethality. But the government is also facing drastic cuts in spending and personnel, driven by the Department of Government Efficiency, or DOGE, run by billionaire Trump adviser Elon Musk. Senators acknowledged the continuing resolution presents a challenge for the military, but they provided no clear answer on whether flexibility will be built in as the spending bill heads to the Senate this week. “From a readiness standpoint, none of us think this is helpful. What would be worse, in my view, is a government shutdown,” said Sen. Dan Sullivan, R-Alaska. Sen. Mazie Hirono, D-Hawaii, questioned whether the deployment of active duty forces to the southern border is impeding training and readiness because troops are largely erecting barriers and helping border agents with intelligence, logistics and other tasks. She said having warfighters “overseeing the stocking of civilian warehouses and data entry on the (CBP computers)” doesn’t sound like the emphasis on lethality that Hegseth has promised.
#dark-rx#Krasnov#donald trump#trump#trump administration#fuck trump#fuck musk#elon musk#musk#nazilism#president musk#president trump#trump 2024#trump is a threat to democracy#anti trump#traitor trump#trump is the enemy of the people
26 notes
·
View notes
Text
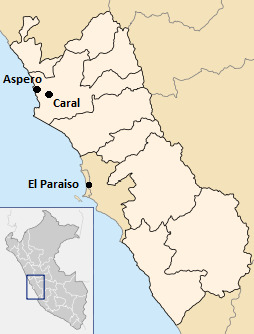
Caral-Supe Civilization
By Ontrvet - Own work, CC BY-SA 3.0, https://commons.wikimedia.org/w/index.php?curid=18736804
The Caral-Supe, also known as the Caral or Norte Chico, are a group of people that lived along the north-central coast of modern-day Peru from 3500-1800 BCE, contemporary to the building of the Egyptian pyramids. They also lived along the Fortaleza, Pativilca, and the Supe rivers. They are considered to be the oldest-known civilization in the Americas, predating cultures like the Olmecs by nearly 2000 years.

By I, KyleThayer, CC BY-SA 3.0, https://commons.wikimedia.org/w/index.php?curid=2441867
Though there was a complex culture, the Caral-Supe people did not leave any ceramics or evidence of other visual arts behind. They did grow cotton with irrigation, which was a very important crop for clothing and nets as their animal protein sources were marine, even among those who lived inland. This reliance on marine protein sources lead to the hypothesis called the "Maritime Foundations of Andean Civilizations' hypothesis (MFAC), in which the culture began on the coast and then moved inland to find and then cultivate cotton to support those on the coast.

By I, Xauxa, CC BY 2.5, https://commons.wikimedia.org/w/index.php?curid=2503267
In addition to maritime protein, the Caral-Supe people also ate squash, beans, guava, and sweet potato, adding avocado and achira in northern areas. More recent studies also show that maize was also grown. Prior to about 2013, it was thought that the Caral-Supe didn't have a staple food that they grew. According to Evidence for maize (Zea mays) in the Late Archaic (3000–1800 B.C.) in the Norte Chico region of Peru published in 2013, 'New data drawn from coprolites, pollen records, and stone tool residues, combined with 126 radiocarbon dates, demonstrate that maize was widely grown, intensively processed, and constituted a primary component of the diet throughout the period from 3000 to 1800 BC.'

By I, Xauxa, CC BY 2.5, https://commons.wikimedia.org/w/index.php?curid=222037
Without an artistic or written record, it's difficult to know a lot about the Caral-Supe culture. They did leave behind a vast wealth of buildings, including large pyramids. They also built settlements close together, making it perhaps the most densely populated area area during the 3rd millennium BCE, with the possible exception of Northern China. Quipu have been found, though exactly how or why they were used is uncertain, as it is with later Andean civilizations.

Credit: Caral Archaeological Zone – Ministry of Culture of Peru
Efforts have been made to extrapolate what type of government the Caral-Supe people had, including the economy, ideology, and physical bases of power would have been. Evidence for a central government include some of the structures being built in one or two large pushes and large warehouses left behind. Other economic evidence include the trade relationships between the inland and maritime groups as well as those living else where as evidenced by 'Caral] exported its own products and those of Aspero to distant communities in exchange for exotic imports: Spondylus shells from the coast of Ecuador, rich dyes from the Andean highlands, hallucinogenic snuff from the Amazon.'

source: https://www.ancient-origins.net/ancient-places-americas/unique-artifacts-shed-light-daily-life-5000-year-old-city-caral-002019
The ideology is harder to pin down because they didn't decorate their buildings. A gourd was found with what appears to be the Staff God, a depiction of a human-like figure holding instruments of power, this one being 'a leering figure with a hood and fangs' and it is the oldest such depiction. As this type of depiction is common among other pre-Colombian Andean societies, it is thought that access to deities and the supernatural was a part of the purpose of government.

By I, Xauxa, CC BY 2.5, https://commons.wikimedia.org/w/index.php?curid=2488467
Physical evidence includes a lack of damage due to warfare, including a lack of bodies that were injured in warfare, nor are there walls around the settlements. The complexity of Caral-Supe culture without the evidence of warfare or need for defense driving kin groups into larger societies is unique among those ancient societies that have been studied. Most complex cultures came about as a way to defend against others.
Further Reading:
Pyramidal structure unearthed in Chupacigarro, Peru
20 notes
·
View notes
Note
What are your zolu hcs?
this is inspired by a scene from the anime during Luffy's flashback post Marineford. It's the way Luffy doesn't cross Zoro's boundaries. At first, Luffy sees a lot of himself in Zoro and that's why he finds that Zoro can take the way he treated him (i.e. the manhandling, flinging around, teasing him relentlessly) and he was right to some degree, Zoro seems to tolerate pain despite not made out of gum so he does sometimes still yanked Zoro when he ran in the wrong direction and stuff like that. Zoro also does the same thing as him, pinching him, bonking foreheads, using his full power to fight Luffy, scolding or teasing Luffy back. But Luffy realizes that Zoro is an immovable force when it comes to things like sleeping or training and he stops bothering him. Sometimes he still asks Zoro to play with him as a way to share his excitement but he doesn't disturb him or poke him or steal his stuff anymore and just tap on Zoro's shoulder or his weight. Luffy doesn't even need to say anything because Zoro already knows what he wants and he also knows that his "clingy" captain likes to do this just for the sake of seeking Zoro. Sorry, it's such a small gesture but I will die on this hill because Luffy cares for Zoro as much as Zoro does for him


they call each other aibous/partners LOL either in the final saga or post-canon or when they get together. Had this idea after a Sabaody arc rewatch and saw RayRoger call each other that. Also why I find a lot of parallels between ZL and KidKiller. I find it even more fitting than right-hand man or vice-captain (but he could be all of them)
Zoro has a weird way with PDA. He doesn't do that much because he gets embarrassed by it. But he can't keep himself away from Luffy's personal space. Probably because Luffy does the same. He likes to sniff him discreetly; swing his leg on top of Luffy, acting like he was just nonchalantly chugging his beer; randomly pin Luffy down with his whole weight and falling asleep on top of him while Luffy looks so confused at first; press a palm on the back of Luffy's neck and pulling him to press their foreheads together while staring intensely into Luffy's eyes; neither of them saying anything until Nami told them to get a room; Zoro likes to bite Luffy, on his shoulder blades or his cheeks, due to cuteness aggression. He is actually the one who started it before Luffy developed a habit of biting him.
In modern AU, I really like to HC kindergarten/daycare/preschool teacher Luffy. His jobs can be pretty diverse, ranging from errand boy, to sex worker, to sumo wrestler, to boxer or MMA, to child care, to delivery service, pet sitter, warehouse operator, oil rig worker, beetle expert/scientist, and (a moot suggested) animal whisperer. Did he get a degree? maybe. Did it take him multiple tries to get a degree? could be. Did Sabo or Nami hook him up with a fake certificate? also possible. He might not even need them, this and that offered him after he helped them or something. While Zoro for me is usually pretty straightforward. A kendo athlete or teacher, anything by Luffy's side, bounty hunter or a hitman, or he gets paid to do the math equations in his classmates' assignments. At one point he was offered a data analysis or statistics job where he didn't last for a week because he got bored, had a bad attitude, and was often late due to getting lost
I have so many zl hcs I have not made any fanwork of, but these are the ones I thought abt at the top of my head so I hope you enjoyed it. Let me know what you think.
Bonus mature one to make this five hcs in total
Luffy bottoms, Zoro tops. Sometimes, Zoro is more of a side or touch-me-not, so they would use toys, hands, or tongues. Luffy looooves Zoro's mouth, almost more than getting dicked down. They either have quickies almost every day or they can go months without having sex so they don't have it planned out and they don't really experiment. One or both of them will just ask the other if they're horny or not, if they want to let off steam or not and just go at it. Zoro finds more pleasure in Luffy's reactions and looks than his own while in return, Luffy lets him in his most vulnerable state and gives him all his unbridled attention. Oftentimes, Zoro does it because he misses Luffy.
45 notes
·
View notes
Text
May Trope Mayhem day 04 @duckprintspress
Modern Au with power/magic story in Mo Dao Zu Shi
Lan Wangji wake-up in a strange place, soon noticing that he was tied to a chair by his arms and legs.
The last thing he remembered was that he just finished his usual patrol and was turning in for the night when some black shadow surrounded him.
Then he awaked
He couldn't see much but it looked like some kind of warehouse, and it was empty for what he could sense. So he started trying to see if he could break the ties binding him, not much luck with his legs but his arms were a possibility.
But when he was going to try freeing himself the shadows around the warehouse started moving.
“I wouldn't do it if I were you”. A melodic voice sings songs behind him. “It's rude to free oneself before we have the chance to talk.”
Straightening his back, Lan Wangji didn't give the other the pleasure of seeing him try to find where the voice was coming from, instead he kept looking forward.
“Who are you?” He asked his captor.
“Oh? I’am pretty sure you know who I am, Hanguang-Jun” The voice came close to him, the shadow thickening and darking. “I know how the league of heroes have being trying to find me, and that you was one of those who are looking”
The last part was whispered close to his ear.
Indeed he was one of the heroes responsible to track and locate one villain that was breaking in the Jin’s research facilities, destroying all the datas and sometimes attacking researchers. The League didn't identify his motives or affiliations, but know that he is using shadows and other abilities and for that they start calling him by one name.
“The Yiling Patriarch” He stated.
“See? Not so difficult.” The smile was clear on his voice. The shadows are dancing around him until they part right in front of him to reveal a tall man, using dark and red traditional clothes with long sleeves, long hair that obscure his face.
Lan Wangji kept silent, staring right ahead, not even bothering to look into the villain's eyes.
“What?” The Yiling Patriarch asked, tilting his head a little. “Nothing to say?”
Lan Wangji just looked at him for a moment, then looked away unimpressed.
“So silence or Hanguang-Jun” the man mused. “That's a shame, handsome but not even a smile.”
Lan Wangji frowned, that get him angry. He turned to the man again, ready to chastised the man for the improper conduct when he sees a little head peeking from behind the man legs.
“Whites ge-ge is very pretty!” confirmed the little voice, surprising the Yiling Patriarch that jumped with wide eyes, shadows clearing instantanly from the warehouse.
“A-Yuan!!!” cries in a much more high voice than when he was talking before, making the child giggle. “What you doing here? I told you to stay in the living room.”
“But the coach is on fire.” The boy stated smiling innocent, no even noticing the serious of the hole situation. The eyes of the man get wide a second time and he flies to somewhere behind were Lan Wangji was sitting.
A door banged loud somewhere.
What was happening? Lan Wangji asked to himself.
He was kidnap by the villan that he was tracking, how apparently have a take a children hostage and was keeping them in a dangerous place that was susceptible to fire.
His contemplations was interrupted when something, or more someone hugged his leg that was still bonded to the chair. Looking down, he sees the boy grinning to him.
“HI! My names A-Yuan!!” The boy chirped.
“Hello A-Yuan, I am Hanguang-Jun.” Lan Wangji says. Normally kids would jump when hearing his hero's name mut the boy just smiled again and stay happily hugging his leg.
He was just to ask the kid if he was alright and what the Yiling Patriarch was doing with him when he heard the said man returning.
“Everything safe! The fire extinction talisman worked” he said apparently to no one in expecific. Then, praisingthe boy he said. “A-Yuan was very smart in come get me, well done”
Then he notice that the boy was hugging Lan Wangji and hunffs.
“Aya, A-Yuan!!” putting his hands in his waist he reprimanded. “What I said about hugging people legs?”
“But I like White ge-ge!!” The boy declared.
“That doesn't make it alright…” the Yiling Patriarch grumbled. Then he picket the kid and hold him sitting in his waist. “What a do with you, uhm?”
“You should give him back to his parents.” Lan Wangji interrupted and the man blinked to him looking like he forgot that he had him hostage.
“Oh? But a birth him myself.” The other replied innocent, and Lan Wangji scolded himself for assuming, until the Yiling Patriarch started laughing. “Ah! You believed! It's a joke…”
A sneeze from A-Yuan cut his speech, then a fire started in his sleeve.
“Oh shit!!” The man jumped and then shadows muffled the flames erasing it. It was quick but was obviously the ability of the child, the problem was:
“He is too young to already have powers.” Lan Wangji state, it's supossed to be a accusation but then the Yiling Patriarch says.
“Indeed, he is.” He's angry. “To young, but the league was using him as a test subject from their research.”
Lan Wangji esitedd. He didn't know about this, the Jin’s were responsible about the research in the league…
“Tell me, Hanguang-Jun.” The Yiling Patriarch challenges. “How can one call yourself a hero when they do this with children?”
“I didn't know nothing about this.” He assured him. “But I swear that I will find the true about it.”
The Patriarch looks him in the eyes for a moment, then probably believe him, because he says.
“Then make sure you do.” He gesture with the hand and the shadows engulfed Lan Wangji again.
He awake in his apartment. Getting up he calls his brother, there's a job to do.
10 notes
·
View notes
Text
I have worked as the sole data analyst here for years and understand our database well enough that I've been asked to fill in for dev to identify site errors on several occasions. I still need to request table access piecemeal from dev, and my requests are almost always met with resistance questioning why I would possibly need the only source for data behind something benign (like order shipments).
after providing my reasoning (it's the only way to get tracking number data) my responses are typically ignored for 4+ weeks before receiving the permission. sometimes my tickets are closed or hang for months and I don't get shit though.
a new warehouse manager dug up a bunch of reports last used nearly a decade ago which pulled data from obsolete tables and woefully depreciated views. he requested access to all of those data sources and received the permissions right away. now im trying to modernize his shit before the info he's using causes problems.
i need a new job.
#i really dont get it#and I'm so fucking tired of trying to decode the secret reasons behind why people vehemently refuse the most basic cooperation#either learn basic communication skills or go live as a hermit
12 notes
·
View notes
Text
dicks keep growing around me - 1 (Myron)
Until recently, Myron was oblivious to the fact that dicks would get mysteriously bigger the longer someone hung out with him. He begins putting the pieces together as his boss, Miguel, starts going through all too familiar changes below the belt.
2 - Next
Also on Metabods
dick growth // huge cock
2222 words
(I couldn't get this phrase out of my head and I thought it was funny, so I'm seeing where it leads)
---
“Dicks keep growing around you?”
“Yes,” I said. “Or at least I think. It’s not exactly an airtight theory, but there are some examples.”
“And it just…happens,” responded my supervisor Miguel.
“Apparently.”
“And it’s happening to me?”
“Pretty sure.”
So I have a theory. Maybe just a hunch, I don’t know. And I’m not doing it on purpose, but I’m pretty sure I’m the cause. For lack of a better way of saying, dicks keep growing around me. And I don’t mean chubbing up, I mean literally growing. Like adding on real, tangible inches with no end in sight. It’s very slow, and I think it comes down to how often we’re in close proximity, but if you spend enough time around me, you may end up with more, sometimes much more, below the belt. I don’t have any idea how this works, but I wish I did. I’m still just piecing clues together.
So I guess Exhibit A would be my boss, Miguel. I do a lot of temporary contract work, which isn’t ideal, but allows me to string together rent while working on some of my own creative freelance stuff. I was hired onto this project six months ago to restructure the data management system of a small, local startup and they miscalculated the resultant shift in office space. After a series of awkward corners and at least one broom closet, they decided to just stick me in Miguel’s office. Miguel requested it actually. He figured I would be of more use working in tandem with him than I would blocking everyone’s path to the bathroom.
I was less than pleased to look like his makeshift corner secretary, and honestly I’ve dealt with much worse, but he didn’t mind. In fact, he seemed to welcome the company. Miguel kept a tight beard and even tighter fade, always perfectly put together in what looked like one-step-below-designer business casual, with the cherry on top being the neon purple and green barefoot shoes he tended to wear to work. I would’ve been annoyed if not for the fact that he was a genuinely nice, thoughtful guy, and more than just a captivating smile. Plus, I came around on his use of a balance ball chair once I was introduced to his tight butt clad in well fitting slacks. Not that I ever really thought about him that way.
So we shared a space and had a congenial enough dynamic. We both had similar tastes in some of the experimental music scene locally and would even go out to some shows together. Also he’s a self professed menswear expert and started systemically giving my wardrobe a much needed overhaul. So I found it odd when his usual form fitting, modern pants began to lose their flair.
At one point, he chalked it up to seasonal shifts, trying out some new, looser looks for the spring. Not to mention baggier, boxier styles had been taking the place of slim fit jeans and tight shirts, at least according to him. A few times he texted me in the morning, saying he was running late because of a ‘wardrobe malfunction,’ which I never thought much of. I had come to expect him cycling through three or four outfit changes before he finally made it out.
For a while it seemed like he might’ve just been getting the wrong fit, since he developed a habit of adjusting his crotch often, or even wincing slightly when he sat down too hard. And I had had multiple friends and partners with similar issues, so offered some tailoring tips, but he didn’t want to dwell on it.
I got a good idea why when we went to a show together one evening. A DJ we both liked was playing a set at a warehouse on a Thursday night, and we figured we had to go. We’d bring a change of clothes, work late on Thursday, then roll into the office late Friday morning. We could even call it a team meeting or professional development or something.
The show was euphoric. I felt like I was rising up and outside of myself as our bodies bounced on the packed dance floor, in so small part due to the haze of surprisingly strong drinks and party drugs. While Miguel seemed to be enjoying it, he was still preoccupied with the constant need to readjust his crotch. I had seen him in this pair of skinny leather pants–his ass alone was unforgettable–but they seemed especially constricting.
“Told you you’d look great in those pants,” came Miguel’s familiar voice in my ear. He never missed an opportunity to brag about being my personal stylist, but I had to admit I looked better than expected. However, I didn’t expect Miguel’s strong hands to linger on my hips, nor did I expect myself to close the rest of the gap between us. I’d been catching guys checking us out all night and I was feeling myself, so I thought Fuck it, as we began grinding to the rhythm. Maybe it was the fantasy of the moment or whatever I was on, but the bulge in Miguel’s pants felt major, and his crotch was radiating heat.
Suddenly, Miguel’s hands tensed up and he pulled away, his hand trailing against my lower back as he turned to leave. I asked if he was doing alright and he sputtered something about needing to piss, quickly disappearing into the crowd. I didn’t think much of it, and quickly got lost in the crush of moving bodies, and more than a few lingering caresses just below my hips. To say I was getting hot and bothered was an understatement and eventually I realized that I also needed to relieve myself, aiming in the vague direction of the bathroom but quickly getting lost in the crush of the crowd. Eventually I stumbled into a back alley, a rush of chill spring night air hitting my lungs as the party thumped through the wall behind me.
I turned my head at the sound of a deep sigh of visceral relief, looking to the left to see Miguel, eyes closed and head thrown back as he pissed loudly against the side of the wall. I wasn’t exactly in my right mind, and didn’t stop myself from glancing at his cock, which, semisoft, was hanging halfway down to his knees, jiggling comically as he shook off the last drops. It wasn’t just massive, it was beautiful, majestic under the streetlight, draped in shadow by Miguel’s outstretched arm, other hand bracing against the wall.
“Sorry,” he said, making me quickly realize that while my eyes were hyperfocused on his schlong, his were on me watching me hyperfocus on his schlong. “There was a line to the bathroom and it was about to be a photo finish,” a slight smile turning up his lips as he saw me finally draw my eyes away from his stunning dick.
“I, uh, was just about to join you,” I replied, deliberately keeping my eyes on his as he struggled to fit his prodigious cock back into his pants, by some miracle getting the zipper up after a few tries.
The awkwardness must’ve been my own anxious imagination, as the next day at work he actually seemed more relaxed than he had in a while, his bubble butt perched on his exercise ball chair as he sat with a leisurely spread, his bulge plainly visible. I guess the secret’s out, I thought. At least between us.
—
When the summer sun had come to stay, and my contract was wrapping up, he proposed an office hiking trip at one of his favorite trails, a moderately strenuous 3.5 mile track that led to an impressive waterfall tucked away just outside the city. I hadn’t been, but was familiar with it because my roommate, Ty, worked in the kitchen at a bar nearby that was kind of the post-hike spot. My apartment, according to Miguel, was “on the way” to the trailhead. I begged to differ, but he insisted on the kind gesture of giving me a lift, until we reached the compromise of me getting a ride home with Ty when their shift ended. So Miguel picked me up from my place, decked out in hiking boots, thick socks, a breezy short sleeve button down, and some five inch linen shorts with a sizable bulge. I had already caught a glimpse of his dick, so I wasn’t surprised by what looked like rolled up tube socks tucked into his crotch, but this looked bigger than I remembered.
And I don’t think I was the only one who noticed either. Miguel was certainly the center of attention when we met up with the others at the trailhead, albeit delightfully oblivious in his excitement to take us on this outing. And it looked like I may have missed the memo about the dress code. All the other guys were wearing similar short shorts, showing off their own respectable bulges–though not as impressive as Miguel’s.
As we set off down the trail, Miguel took an early lead, looking like he had no intention of slowing down. As we settled into a rhythm, I found myself consistently a few steps behind him–admiring more than the view of the scenery–with the rest of the group farther back but still within earshot. I began to think that Miguel should’ve stuck to the breezy bottoms he had fallen into wearing, because he was constantly adjusting the hem of his shorts as they dug into his meaty quads. At times, he seemed visibly uncomfortable.
As we reached a bend in the trail with a makeshift bench, we decided to take a breather and let the others catch up. Miguel’s shirt was glued to the middle of his back by a trail of sweat that ran down to his butt crack. I had trouble noticing anything else as he bent over and rested his hands on his knees, pushing his tight butt in my direction as he caught his breath.
From behind, the crotch of his pants looked overstuffed and straining at the seams. I thought it must have been my exhausted brain and overactive imagination until with a soft rip, the crotch of his shorts gave out, his dick gracefully bobbing two thirds of the way to his knees, definitely bigger than before and paired with some proportionately huge nuts. Miguel, his cock now freed of its constraints, let out a sigh of relief before apparently coming to the realization of the cool breeze on his oversized genitals.
Hearing the others approaching, I sprang into action, pushing him off the trail and just behind a stand of bushes, hoping passers by would assume he was relieving himself and keep moving.
“Sorry,” he said. “I brought up a backup pair just in case, give me one second.”
“A backup pair?” I asked, wanting to respect his privacy but also betraying my own fascination with this super dick that I had now been introduced to twice.
“Yeah, I thought I wouldn’t have an issue yet with these pants, but wanted to be careful.”
“What do you mean issue?” I asked. “And what do you mean yet?”
“I don’t know, I think I need to see somebody about this, it’s like–” he was cut off by one of their co-workers catching up to them on the trail. He quickly finished changing and stuffed his cock back in his shorts, shooting me a brief look of thanks.
—
Thankfully, the rest of the outing passed without incident. We actually had a great time, and Miguel was certainly correct about the waterfall being worth the aggravation. A few of the guys even waded in to cool off, inadvertently revealing some very heavy bulges through the thin, wet fabric of their shorts. Miguel hung back.
We got drinks afterward and it was obvious Miguel was a post-hike usual. As the afternoon wore on to evening, everyone fell away slowly, until it was just the two of us. He insisted on hanging around until Ty could take me home, and I would’ve staunchly refused if not for how much I enjoyed his company–and how he would’ve stayed against my wishes anyways.
He hadn’t really been drinking–concerned about everyone else having a good time, in typical Miguel fashion–but I had maybe had more than I should. During a lull in the conversation, he leaned in slightly and said “Thanks for the save back there. Would’ve never lived it down at work.”
“To be honest, I was not expecting all that,” I said, trying to be careful not to push boundaries too far too fast.
“Honestly, me neither,” Miguel responded, his eyes widening slightly as he glanced into the distance. “TMI, but I’ve been kind of having a late growth spurt the last six months. Or something.”
And well, this is when the pieces finally started to come together. I had had hunches and musings over the years about my propensity to meet some truly noteworthy cocks, but something deep in my brain felt compelled to ask “When did it start?”
With a thoughtful look in his eye, he glanced at me and said, “Around when you showed up. You might be my lucky charm.”
This is when it finally clicked.
58 notes
·
View notes
Text
Warehouse Buzzer System
How Electronic Message Boards Assist In Updating

Electronic message boards are fairly prevalent today, and their usage seems to be proliferating. Message boards in electronic kind properly interact swiftly upgraded company memoranda, final timetable modifications, and marketing, three fairly various applications providing one an idea of the breadth that this medium has gotten to. Herein we explore the phenomenon both generally and in regards to the power released when incorporated with an integrated clock system.
Electronic message boards derive from a lengthy background of open-air communication making use of indicators, billboards, marquees, and so on. Trick attributes were the layouts utilized and the feedback time for updating info. The most usual style entailed drawing on comprehensive personality collections, containing letters, numbers, and spelling, to create words, hanging them from hooks or resting them on wooden slats.
Posts were changed by hand, and updates were thus irregular. In time, updating was improved and somewhat automated using electronic control, such as seen with old baseball park scoreboards.
However, there was still the danger of lacking specific characters and being rendered unable to display all words in your message. This problem was addressed when the dot matrix selection was created, which stood for any type of character (in any type of typeface)-- also graphics-- with a rectangular pattern of on-or-off dots. These could be published on paper, yet a lot more effective was to present them in grids of light bulbs or on a screen.
Mapping formulas converted text into ranges of dots virtually instantaneously, and while drivers entered on a console, messages scrolled across the screen in essentially live. This system still required manual work, however the display screen tool was much easier to read, new, and updatable in a matter of moments. Whence the birth of electronic message boards that utilized light bulbs as the dots, or pixels.
Early light bulbs were incandescent, and were really the only choice; nonetheless, they had brief life-spans and prone to failing from shock. By the millenium, light producing diodes (LED) were a fully grown innovation and available in several shades, including white. Additionally, they outlived incandescent light bulbs by approximately 50 times, were not so breakable, and rapidly came to be the recommended part for message boards.
In time developers got extra creative with the tool and wanted to have more than one "on" shade to deal with. LEDs can fulfill this desire with their 3-in-1 mix of the 3 primary colors to synthesize white light; by choosing different sub-combinations you can obtain 7 various shades.
At some point, upgrading had to transition out of its humble manual origins. Now, textual info can be gotten in real time or gotten from data sources, and software is utilized to map the information right into matrices of (color-coded) dots that get buffered and presented quickly, effortlessly, and effortlessly. Graphics can be incorporated if they are mapped in advance.
Therefore, the modern digital boards are essentially automated, though there are provisions for bypassing scheduled programs with brand-new content in emergencies. Synchronous timekeeping systems manage everything.
An intriguing advancement is the integration of sound signals with the visual information being displayed on a sign in either textual or visual kind. It is popular that a close coordination of both kinds of sensuous stimulations has a tendency to get the message throughout many successfully. It's not a combination of both elements into tune, yet rather the use of sounds (bells, tones, whistles) as focus grabbers to change emphasis of the target market to what the board is showing, whether it be information or other timely information. synchronized clocks for hospitals
The world has actually expanded tired with fixed messaging in regards to both web content and style. Things need to be vibrant to sign up, and this needs constant educational updates. With this article we have seen exactly how electronic message boards promote updating.
youtube
2 notes
·
View notes
Text
What are the Advantages of Data Warehouse Modernization in 2024?

Unlock the potential of your business data with our blog on data warehouse modernization. Learn the benefits, steps, and reasons to upgrade for better decisions and performance.
0 notes